Get to know more about Wazuh
Wazuh is a fork of the OSSEC HIDS(Host-Based Intrusion Detection System) project. Wazuh grants a free, open-source platform to small and big enterprises for incident response, threat detection, integrity monitoring, and compliance verification. Its centralized and cross-platform architecture aided in monitoring multi-platform agents, cloud services, containers, and aggregating and analyzing data from other external sources(like firewall, routers, switches, etc.) Its usage became famous for its integration with elastic stack and OpenSCAP, which extended its functionality.
Main Features
- Intrusion Detection
Wazuh agent scans the monitored system for rootkits, malware, suspicious anomalies. They can detect unregistered network scanners, hidden files, suspicious processes, and inconsistencies in system call responses. Apart from agent capabilities, the master server has components that collect agent data and look for compromise indicators.
- File Integrity Monitoring
Wazuh monitors filesystem and detects changes in permission, ownership, changes in content, attributes of essential files.
- Log and Security Analysis
Wazuh agents scan the operating system and application logs and securely forward the real-time data to the master server. The collected data will be processed based on the rules, aggregated, indexed, and stored for easy analysis for any security anomalies.
- Vulnerability Detection
Wazuh agent pulls software inventory data and sends it to the master server. It becomes correlated with continuously updated CVE(Common Vulnerabilities and Exposure) databases, thus identifying any vulnerable software in the monitored system.
- Regulatory Compliance
Wazuh provides necessary security controls to become compliant with various industry standards and regulations. It is widely used by companies to meet PCI DSS requirements.
- Cloud Security Monitoring
Wazuh can monitor cloud infrastructure at an API level using its integration modules that collect security data from all major cloud service providers like AWS, Azure, google cloud, etc. and detect any security weakness.
- Container Security
Wazuh can monitor the Docker host and containers for vulnerabilities. Wazuh agent has native integration with Docker to monitor its components.
- Active Response
Wazuh provides an active response module to handle an automatic response to specific alerts that you configure on the Wazuh-manager. The above capabilities are achieved by Wazuh with the integration of OSSEC, Elastic Stack, and OpenSCAP, providing a centralized configuration that is easy to manage. Wazuh provided an updated ruleset for log analysis and a RESTful API. It also provides a Kibana application that has a friendly web interface for managing Wazuh infrastructure.
BASIC ARCHITECTURE AND COMPONENTS
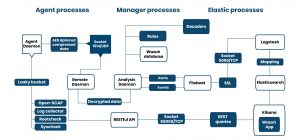
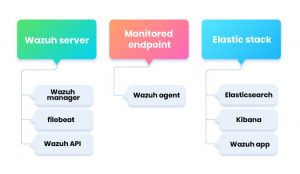
The main components of Wazuh are the wazuh agent, which runs on all monitored agents, the wazuh server which collects, analyses the data sent by wazuh agent, and agentless sources. Wazuh server forwards this data to Elastic stack where it gets indexed and stored for user-level logical analysis.
Fig.1 Data Flow Diagram
- Wazuh Agent
It can run on all primary OS like Windows, Linux, Solaris, BDS, MAC, etc. The primary duty is to collect monitoring data from the monitored agents(physical servers, VMS, docker containers, cloud instances, etc.) and send them to the master server (Wazuh server). Wazuh agent capabilities come from its various processes listed below.
- Root check: Detects rootkits, malware, system anomalies, and other necessary security checks
- Log Collector: Collects operating system and application log, windows event logs, etc
- Sys check: Does file integrity check
- OpenSCAP: This module can use the system for vulnerable applications or configuration.
- AgentDaemon: It collects data from all other agent components and sends to master server via a secure channel
- Wazuh Server
Wazuh server is responsible for analyzing data sent by Wazuh agents and trigger alerts based on predefined rules. Below are the main server components:
- Registrative service: We use this to register each agent by provisioning and to distribute pre-shared keys.
- Remote Daemon service: This service receives data from the agent and ensures secure communication between the master and agent.
- Analysis Daemon: This process performs data analysis.
- RESTful API: This provides an interface for managing and monitoring agent deployment and configuration status.
ELK Stack It is the combination of open-source log management tools, Elastic search, Logstash, and Kibana.
- ElasticSearch: Transformed data from logstash is indexed, stored, and works as a search engine for retrieving it when required. NoSQL based database queries based on Apache Lucene. It is scalable.
- Logstash: Collects and events data and can parse and transform it.
- Kibana: It is a flexible and intuitive web interface for data mining, monitoring, and visualization.
- Filebeat: Filebeat is a lightweight forwarder used to convey logs across a network, usually to Elasticsearch.
Wazuh architecture works on agents running on monitors hosts(agents or agentless) that forward data to the Wazuh server. Based on the requirement, we follow Single-Host or Distributed architecture. Suppose the number of monitored is less than 50. In that case, we usually go for single cluster architecture where Wazuh Server, ELK stack, is deployed on the same server and Wazuh agents in the monitored host. If the number of monitored hosts is large, the Wazuh server and ELK stack clusters are deployed in a different server, as shown in Fig.2, which uses filebeat for communication.
Fig.2 Distributed Architecture
Wazuh Competitors or Alternatives: Ossec, Graylog, Splunk, ELK, Osquery, etc.
Why choose Wazuh?
- Opensource
- It can integrate with WordPress, Cloudflare, Linux, Windows, and Splunk, ELK, etc.
- Improved ruleset
- RESTful API
- Integration of PCI DSS and other compliance
- Main Features discussed earlier
- Cross-platform support, well documented
For business or enterprises that need to meet the compliance requirements (such as PCI DSS or HIPAA) and configuration standards (CIS hardening guides) has this brilliant platform to work. With regular updates and integration with new technology, it is now popular among IaaS users (e.g., Amazon AWS, Azure, or Google cloud.) who deploy host-based IDS in the running instances combined with the analysis of the infrastructure events. Wazuh is an excellent solution for small or large enterprises, as it is open-source and free.
– By PRASOON RAJ A
DevOps Engineer